As per Gartner, 70% of businesses in regulated industries will have compliance included into their DevOps toolchains by 2026, lowering risk management and enhancing lead times by at least 15%.
Organizations required to update their outdated procedures, which led to the development of automated DevOps compliance tools, checklists, and playbooks are examples of implementation techniques that are error-prone and restrict delivery value streams. When adopting these strategies, violations frequently happen late in the SDLC, leading to expensive errors that are challenging to fix. Although the operational environment has always required compliance remediation and reporting, prior techniques for doing so have frequently been separated from delivery pipelines.
The ability to identify drift or violations early in the delivery cycle, prioritize them wisely, and provide evidence of compliance necessitates more context, which is challenging to produce without automation. Automating will be more important to I&O leaders as organizations face greater regulatory requirements.
I&O leaders assure repeatability and increased delivery throughput while lowering risks and rule violations by codifying and automating complex rules and regulations using compliance automation solutions.
DevOps Compliance Automation Tools
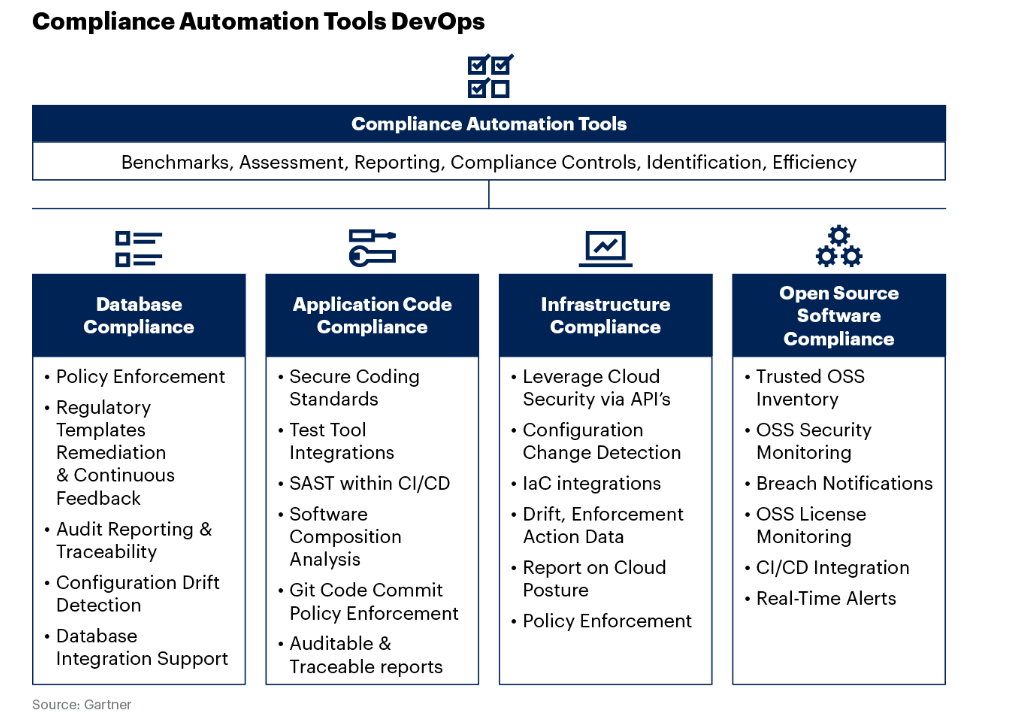
Automated Database Compliance
Processes for delivering software might be hampered by the complexity of data security and compliance if the proper procedures and tooling platforms are not in place. I&O leaders must strike a compromise between the necessity for thorough data security standards and the demand for quickly delivering value to consumers.
Automated DevOps compliance tools can work safely on databases both independently and in collaboration with database administration teams thanks to vendor products in this domain that codify compliance requirements by employing a shift-left approach to testing. These technologies also employ a shift-right testing methodology for audits and reporting to offer proof of production operations subject to legal requirements.
Automation of Application Code
Agile and DevOps-implementing organizations need quicker compliance reviews, but developers are frequently more focused on creating and delivering new apps and capabilities than they are on learning about best practices and coding standards. So, in order to protect the organization, developers want a secure, unrestricted operating environment with automated guardrails and rule enforcement processes.
Application code compliance can be enforced by organizations employing AST technologies. However, a new class of tools that abstract the underlying AST tools offer the following advantages:
- Using static application security testing (SAST)/DAST/IAST technologies in a plug-and-play manner. Application code compliance tools connect with a continuous integration/continuous delivery (CI/CD) toolchain and serve as an abstraction layer over various AST tools.
- Support for GitOps workflows and infrastructure-as-code: Applications and infrastructure, expressed as code in source control can both have problems, which are detectable via application code compliance tools.
- Instruments for orchestrating and correlating application security: By automating operations, these technologies simplify testing for and fixing software vulnerabilities. They automate security testing by ingesting data into a database from several sources, including SCA, vulnerability assessments, static, dynamic, and interactive testing (SAST/DAST/IAST), and others.
Beyond only aggregating vulnerability output, certain ASOC systems can also act as an orchestration layer for various AST tools and non security SDLC tools. In order to centralize and prioritize repair activities, ASOC tools connect and analyze findings.
Automation of Infrastructure
In order to implement infrastructure-as-code, infrastructure DevOps compliance tools are utilized in conjunction with infrastructure automation (IA) tools. I&O teams may design security and compliance policies as code using these technologies, find problems before they affect production, and fix configuration drift and policy violations.
By importing data on compliance, configuration drift, and enforcement actions into SAST IT systems, infrastructure automation technologies enforce security regulations. These technologies also identify adjustments that increase the likelihood of misconfiguration. I&O leaders may find and fix policy violations early in the SLDC by incorporating policy checks into infrastructure-as-code tools and CI/CD pipelines before building production environments.
Infrastructure compliance automation technologies also offer rule modeling that is mapped to sector laws when developing cloud platforms, pre deployment checks and live, autonomous checks to continuously validate compliance are used.
Compliance with Open-Source Software (Using SCA)
In addition to raising the danger of unpatched vulnerabilities, the use of indiscriminate, unmanaged OSS directly in application code or in infrastructure components puts users at risk legally due to the usage of constrictive licenses. A bill of materials for the application is provided by SCA tools to help determine whether the use of any OSS is against organizational policies. This is accomplished by including SCA technologies into the DevOps compliance tools chain.
Applications are analyzed using SCA tools to find commercial, third-party, or open-source software components that have known security and/or functionality flaws. It facilitates safe application development and assembly by ensuring that the business software supply chain only uses secure components.
Scaling DevOps compliance tools call for regular management and upkeep, particularly when the toolchains contain OSS technologies. Unpatched vulnerabilities and license violations brought on by poor OSS governance can put businesses at risk for legal and security issues. Software bills of materials enhance both proprietary and open-source code’s visibility, transparency, security, and integrity in software supply chains. Integrate SBOMs into the entire software delivery life cycle to reap these benefits (see Innovation Insight for SBOMs). Although exporting code that uses or links to OSS necessitates a compliance check, using OSS tools in the toolchain does not violate licensing.
Tools for Compliance Automation
The main goal of DevOps compliance tools is to increase efficiency in the evaluation, management, reporting, and identification of controls that are required by various regulatory frameworks. Tools for automation don’t actually carry out compliance process tasks.
Although the toolchain receives the majority of the attention, both the I&O leader, whose team produces the data, and the stakeholders who use it can benefit greatly from increased productivity.
Incorporating automation technologies into the delivery pipelines for DevOps compliance tools projects provides quick, actionable feedback to developers and creates a chain of provenance for product delivery that continually captures compliance data throughout the pipeline execution.
Rundown
Incorporating continuous automation tools into the DevOps workflow is crucial for modern software development. These tools not only enhance security and reduce compliance-related risks but also enable organizations to deliver software more efficiently and reliably. By automating checks and remediation, development and operations teams can focus on innovation, customer value, and accelerating the pace of software delivery without compromising on security standards.