Oracle continues to make progress with shifting its business model and customer base toward the cloud, albeit with variation in pace across product lines. To accelerate the movement, Oracle is has been adding more “cloud-friendly” attributes to its strategy and execution.
The 4 pillars of Oracle Cloud Infrastructure, the foundation on which it is built:
- Outstanding Price Performance
- Secure By Design – Security First OCI starts with a zero-trust architecture
- The Open Cloud for Enterprise Interoperability Deep Enterprise
- Deep Technology Experience
With this Ebook IT decision Makers and Technology, evaluators will get key Gartner reflections on Oracle’s impressive improvement in Oracle Cloud Infrastructure capabilities. Consequently, they will have enough reasons to consider Oracle in their next public cloud decision.
Oracle has put the security of critical workloads at the forefront of its cloud design. For customers running security-sensitive workloads, Oracle Cloud Infrastructure is a security-first public cloud with robust security architecture and a deep set of rich defense-in-depth capabilities to reduce risk and attack surfaces.
Oracle Cloud Infrastructure has built security in the architecture, data center design, personnel selection, and in the processes for provisioning, using, certifying, and maintaining OCI infrastructure. Security First OCI starts with a zero-trust architecture.
In this eBook Gartner has recognized:
- OCI Dedicated Region C@C offers a full OCI in-region implementation, with all OCI public cloud services available and delivered identically to a customer’s data center (on-premises or colocation). This includes an isolated control plane and isolated self-service interfaces while your data is guaranteed to stay within your region, and continues to function even when the network connection is lost.
- OCI meets typical enterprise expectations for cloud security, including a notable integration with the Oracle CASB Cloud service (Cloud Access Security Broker)

Oracle Cloud Infrastructure (OCI) Security
– The Place for Your Critical Workloads
Security designed for, sensitive, business-critical workloads at the forefront of Oracle Cloud Infrastructure (OCI)
Security By Design
Second-generation Infrastructure-as-a-Service (IaaS) offering which was conceived and architected with security as a primary design principle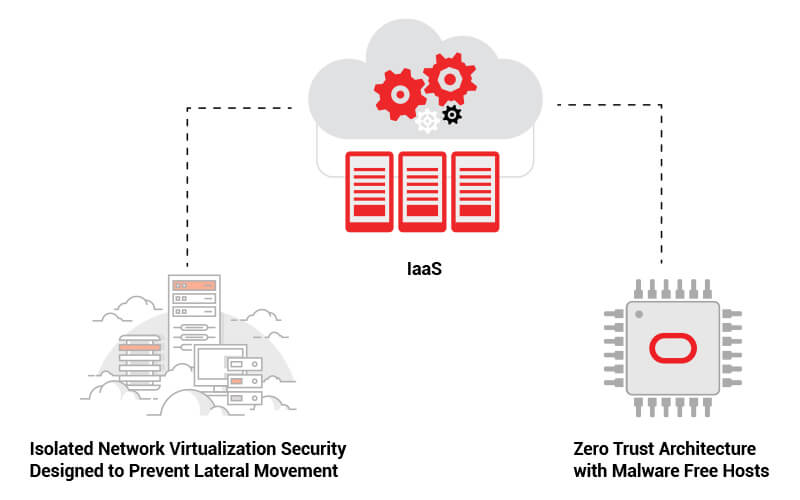
Benefits of Isolated Network Virtualization Security
Prevent attacks on customer tenancies with isolated network virtualization. A foundational element of Oracle Cloud infrastructure’s security-first architecture, Isolated network virtualization stops malware in its tracks with a custom-designed SmartNIC to isolate and virtualize the network.
- Prevent attacks from compromising the network – This was one of the shortcomings of first-generation clouds. In first-generation cloud offerings, if a successful attack compromises a virtual machine instance and subsequently a hypervisor, there are no barriers to prevent an attacker’s attempts to modify the network. The networking function is managed by the same hypervisor that has been compromised: a virtual machine escape that gains access to the hypervisor also has access to the network. This can lead to several threats to hosts on the network and could expose private tenant data.
- Isolate and virtualize the network to prevent attacks – Here the second-generation cloud has an advantage with Oracle Cloud Infrastructure, different from first-generation clouds because of its use of a custom-designed SmartNIC that isolates and virtualizes the network.
The SmartNIC is isolated by hardware and software from the host, preventing a compromised instance from compromising the network. Oracle Cloud Infrastructure maintains greater external control of host network functionality and can prevent network traversal attacks.
Benefits of Zero Trust Architecture with Malware Free Hosts
As the use of cloud services rapidly expands, it also creates new potential for compromised or stolen credentials of a privileged administrator or application. Additionally, it can open the potential for data theft, and cyber criminals to conduct cyber fraud, as effective security controls are often an afterthought. Zero trust makes it possible for organizations to regulate access to systems, networks, and data without giving up control.
- Work From Anywhere Productivity – Empower your users to work more securely anywhere and anytime, on any device.
- Cloud migration – Enable digital transformation with intelligent security for today’s complex environment.
- Risk mitigation – Close security gaps and minimize risk of lateral movement.
Oracle Cloud Infrastructure Earned Trust
Cloud Infrastructure Security with a focus on data protection and securing the paths to access sensitive data. Reduce the risk of firmware-based attacks against Oracle Cloud Infrastructure customer tenants with custom-built, hardware-based root of trust technology.
- Protect customer tenants from firmware-based attacks – Hardware technology customized to deploy clean firmware for every new tenancy.Reduce the risk of firmware-level attacks against cloud tenants with root of trust technology designed to wipe and reinst all the firmware every time a new server is provisioned or a new customer tenancy is established.
- Reduce risk from attacks or backdoors in firmware – Cleans and power cycles each new server. Reduces the risk from a permanent denial of service (PDoS) attack or attempts to embed backdoors in the firmware by power cycling the hardware host, installing the firmware, and confirming the process has been performed as expected for every new server.
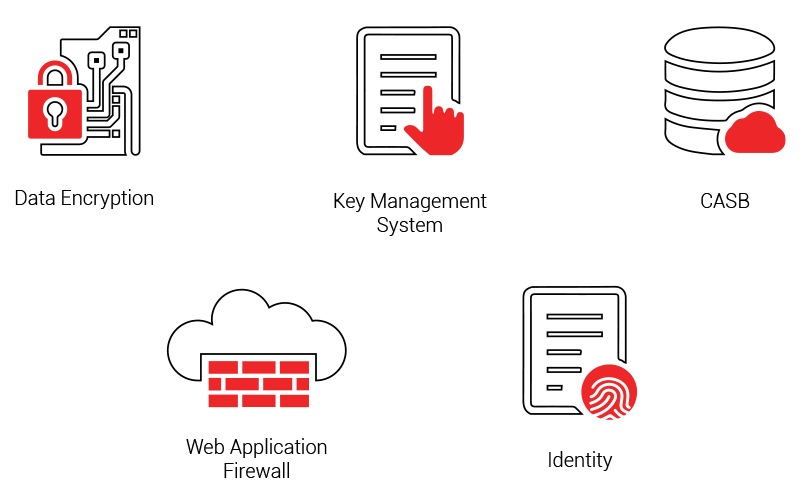
Defense in Depth
Why IT Convergence?
IT Convergence can help you assess what efforts you need to make in order to have an effective migration to the cloud. Within 48 hours, we can look at your current EBS landscape and determine which business process will work and which won’t. In addition our real time Impact Analysis solution can be used for patches and customization and thus testing/defect and requirement management before/during and after the cloud transition. Learn More
- OCI certified company & personnel
- OCI IP, Scripting & Automation for EBS
- Bundled OCI IaaS, OCI PaaS & ITC PaaS solutions with flexible solution design
- Productivity gains resulting in lower labor requirements
- Inflight database upgrades & operating system migrations

